Add-DnsClientNrptRule
Add-DnsClientNrptRule is accessible with the help of DnsClient module. To configure DnsClient, go through this link.
Synopsis
Adds a rule to the NRPT.
Description
The Add-DnsClientNrptRule cmdlet adds a Name Resolution Policy Table (NRPT) rule for the specified namespace.
Parameters
-AsJob
Runs the cmdlet as a background job. Use this parameter to run commands that take a long time to complete.
The cmdlet immediately returns an object that represents the job and then displays the command prompt. You can continue to work in the session while the job completes. To manage the job, use the *-Job cmdlets. To get the job results, use the Receive-Job cmdlet.
For more information about Windows PowerShell background jobs, see about_Jobs.
| Type: | SwitchParameter |
| Position: | Named |
| Default value: | None |
| Accept pipeline input: | False |
| Accept wildcard characters: | False |
-CimSession
Runs the cmdlet in a remote session or on a remote computer. Enter a computer name or a session object, such as the output of a New-CimSession or Get-CimSession cmdlet. The default is the current session on the local computer.
| Type: | CimSession[] |
| Aliases: | Session |
| Position: | Named |
| Default value: | None |
| Accept pipeline input: | False |
| Accept wildcard characters: | False |
-Comment
Stores administrator notes.
| Type: | String |
| Position: | Named |
| Default value: | None |
| Accept pipeline input: | True |
| Accept wildcard characters: | False |
-Confirm
Prompts you for confirmation before running the cmdlet.
| Type: | SwitchParameter |
| Aliases: | cf |
| Position: | Named |
| Default value: | False |
| Accept pipeline input: | False |
| Accept wildcard characters: | False |
-DAEnable
Indicates the rule state for DirectAccess.
| Type: | SwitchParameter |
| Aliases: | DirectAccessEnabled |
| Position: | Named |
| Default value: | None |
| Accept pipeline input: | True |
| Accept wildcard characters: | False |
-DAIPsecEncryptionType
Specifies the Internet Protocol security (IPsec) encryption setting for DirectAccess. The acceptable values for this parameter are:
- None
- Low
- Medium
- High
| Type: | String |
| Aliases: | DirectAccessQueryIPSSECEncryption |
| Accepted values: | , None, Low, Medium, High |
| Position: | Named |
| Default value: | None |
| Accept pipeline input: | True |
| Accept wildcard characters: | False |
-DAIPsecRequired
Indicates that IPsec is required for DirectAccess.
| Type: | SwitchParameter |
| Aliases: | DirectAccessQueryIPsecRequired |
| Position: | Named |
| Default value: | None |
| Accept pipeline input: | True |
| Accept wildcard characters: | False |
-DANameServers
Specifies an array of DNS servers to query when DirectAccess is enabled.
| Type: | String[] |
| Aliases: | DirectAccessDnsServers |
| Position: | Named |
| Default value: | None |
| Accept pipeline input: | True |
| Accept wildcard characters: | False |
-DAProxyServerName
Specifies the proxy server to use when connecting to the Internet. This parameter is only applicable if the DAProxyType parameter is set to UseProxyName.
Acceptable formats are:
- hostname:port
- IPv4 address:port
- IPv6 address:port
| Type: | String |
| Aliases: | DirectAccessProxyName |
| Position: | Named |
| Default value: | None |
| Accept pipeline input: | True |
| Accept wildcard characters: | False |
-DAProxyType
Specifies the proxy server type to be used when connecting to the Internet. The acceptable values for this parameter are:
- NoProxy
- UseDefault
- UseProxyName
| Type: | String |
| Aliases: | DirectAccessProxyType |
| Accepted values: | , NoProxy, UseDefault, UseProxyName |
| Position: | Named |
| Default value: | None |
| Accept pipeline input: | True |
| Accept wildcard characters: | False |
-DisplayName
Specifies an optional friendly name for the NRPT rule.
| Type: | String |
| Position: | Named |
| Default value: | None |
| Accept pipeline input: | True |
| Accept wildcard characters: | False |
-DnsSecEnable
Enables Domain Name System Security Extensions (DNSSEC) on the rule.
| Type: | SwitchParameter |
| Aliases: | DnsSecEnabled |
| Position: | Named |
| Default value: | None |
| Accept pipeline input: | True |
| Accept wildcard characters: | False |
-DnsSecIPsecEncryptionType
Specifies the IPsec tunnel encryption settings.
| Type: | String |
| Aliases: | DnsSecQueryIPsecEncryption |
| Accepted values: | , None, Low, Medium, High |
| Position: | Named |
| Default value: | None |
| Accept pipeline input: | True |
| Accept wildcard characters: | False |
-DnsSecIPsecRequired
Indicates the DNS client must set up an IPsec connection to the DNS server.
| Type: | SwitchParameter |
| Aliases: | DnsSecQueryIPsecRequired |
| Position: | Named |
| Default value: | None |
| Accept pipeline input: | True |
| Accept wildcard characters: | False |
-DnsSecValidationRequired
Indicates that DNSSEC validation is required.
| Type: | SwitchParameter |
| Position: | Named |
| Default value: | None |
| Accept pipeline input: | True |
| Accept wildcard characters: | False |
-GpoName
Specifies the name of the Group Policy Object (GPO).
- If this parameter and the Server parameter are specified, then the NRPT rule is added in the GPO of domain. The Server parameter specifies the domain controller (DC).
- If neither this parameter nor the Server parameter is specified, then the NRPT rule is added for local client computer.
- If this parameter is specified and the Server parameter is not specified, then the DC of the domain specified by this parameter value is found and NRPT rule is added to the GPO.
- If this parameter is not specified and the Server parameter is specified, then an error is displayed.
| Type: | String |
| Position: | Named |
| Default value: | None |
| Accept pipeline input: | True |
| Accept wildcard characters: | False |
-IPsecTrustAuthority
Specifies the certification authority to validate the IPsec channel.
| Type: | String |
| Aliases: | IPsecCARestriction |
| Position: | Named |
| Default value: | None |
| Accept pipeline input: | True |
| Accept wildcard characters: | False |
-NameEncoding
Specifies the encoding format for host names in the DNS query. The acceptable values for this parameter are:
- Disable
- Utf8WithMapping
- Utf8WithoutMapping
- Punycode
| Type: | String |
| Accepted values: | Disable, Utf8WithMapping, Utf8WithoutMapping, Punycode |
| Position: | Named |
| Default value: | None |
| Accept pipeline input: | True |
| Accept wildcard characters: | False |
-NameServers
Specifies the DNS servers to which the DNS query is sent when DirectAccess is disabled.
| Type: | String[] |
| Position: | Named |
| Default value: | None |
| Accept pipeline input: | True |
| Accept wildcard characters: | False |
-Namespace
Specifies the DNS namespace.
| Type: | String[] |
| Position: | 1 |
| Default value: | None |
| Accept pipeline input: | True |
| Accept wildcard characters: | False |
-PassThru
Returns an object representing the item with which you are working. By default, this cmdlet does not generate any output.
| Type: | SwitchParameter |
| Position: | Named |
| Default value: | None |
| Accept pipeline input: | False |
| Accept wildcard characters: | False |
-Server
Specifies the server hosting the GPO. This parameter is only applicable with the GpoName parameter.
| Type: | String |
| Position: | Named |
| Default value: | None |
| Accept pipeline input: | True |
| Accept wildcard characters: | False |
-ThrottleLimit
Specifies the maximum number of concurrent operations that can be established to run the cmdlet. If this parameter is omitted or a value of 0 is entered, then Windows PowerShell calculates an optimum throttle limit for the cmdlet based on the number of CIM cmdlets that are running on the computer. The throttle limit applies only to the current cmdlet, not to the session or to the computer.
| Type: | Int32 |
| Position: | Named |
| Default value: | None |
| Accept pipeline input: | False |
| Accept wildcard characters: | False |
-WhatIf
Shows what would happen if the cmdlet runs. The cmdlet is not run.
| Type: | SwitchParameter |
| Aliases: | wi |
| Position: | Named |
| Default value: | False |
| Accept pipeline input: | False |
| Accept wildcard characters: | False |
Syntax
Add-DnsClientNrptRule [-GpoName <String>] [-DANameServers <String[]>] [-DAIPsecRequired] [-DAIPsecEncryptionType <String>] [-DAProxyServerName <String>] [-DnsSecEnable] [-DnsSecIPsecRequired] [-DnsSecIPsecEncryptionType <String>] [-NameServers <String[]>] [-NameEncoding <String>] [-Namespace] <String[]> [-Server <String>] [-DAProxyType <String>] [-DnsSecValidationRequired] [-DAEnable] [-IPsecTrustAuthority <String>] [-Comment <String>] [-DisplayName <String>] [-PassThru] [-CimSession <CimSession[]>] [-ThrottleLimit <Int32>] [-AsJob] [-WhatIf] [-Confirm] [<CommonParameters>]
—————EXAMPLE 1—————
Add an NRPT rule to a GPO
PS C:>Add-DnsClientNrptRule -GpoName “TestGPO” -DANameServers “10.0.0.1” -DAIPsecRequired -DAIPsecEncryptionType “High” -DAProxyServerName “DaServer.TOSSolution.com:6666” -DnsSecEnable -PassThru -DAProxyType “UseProxyName” -DnsSecValidationRequired -DAEnable -IPsecTrustAuthority “RootCA” -Comment “Sample NRPT Rule” -DisplayName “Sample” -DnsSecIPsecRequired -DnsSecIPsecEncryptionType “Medium” -NameServers “10.0.0.1” -NameEncoding “Punycode” -Namespace “dnsnrpt.TOSSolution.com” -Server “host1.com”
This command adds an NRPT rule in TestGPO on server host1.com for the namespace dnsnrpt.TOSSolution.com.
————–EXAMPLE 2—————
Add an NRPT rule to configure a server
PS C:\>Add-DnsClientNrptRule -Namespace “pqr.TOSSolution.com” -NameServers “10.0.0.1”
This command adds an NRPT rule that configures the server named 10.0.0.1 as a DNS server for the namespace pqr.TOSSolution.com.
————–EXAMPLE 3—————
Add an NRPT rule to enable DNSSEC queries
PS C:\>Add-DnsClientNrptRule -Namespace “pqr.TOSSolution.com” -DnsSecEnable
This command adds an NRPT rule that enables DNSSEC queries to be sent for the namespace pqr.TOSSolution.com.
————–EXAMPLE 4—————
Add an NRPT rule to enable DNSSEC queries for a specified namespace
PS C:\>Add-DnsClientNrptRule -Namespace “pqr.TOSSolution.com” -DnsSecEnable -NameServers “10.0.0.1”
This command adds an NRPT rule that enables DNSSEC queries to be sent to DNS server named 10.0.0.1 for the namespace pqr.TOSSolution.com.
You can check the Version, CommandType and Source of this cmdlet by giving below command.
Get-Command Add-DnsClientNrptRule
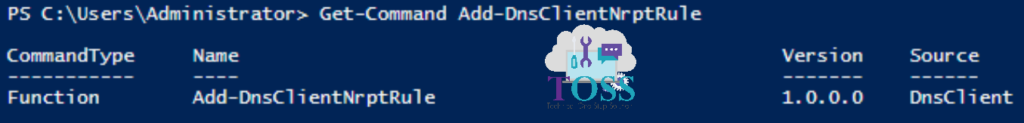
You can also read about
- Get-DnsClientNrptGlobal
- Get-DnsClientNrptPolicy
- Get-DnsClientNrptRule
- Remove-DnsClientNrptRule
- Set-DnsClientNrptGlobal
- Set-DnsClientNrptRule
To know more PowerShell cmdlets(Commands) on DnsClient click here