AWS Client VPN configuring the DUO’s MFA
Most of the time we use OpenVPN and their license for VPN with MFA(Multi-Factor Authentication), which will increase an cost of additional EC2 and OpenVPN license. So this will help you to use AWS Client VPN which is very less cost and Configuring DUO’s for MFA.
Follow the below simple steps to Configure the same. If you have stuck in any step let us know in the comments we will help you.
Step 1 : On DUO’s Admin page
Login to DUO’s admin > go to Application > Click on Protect an application
Select Radius

It will create a Radius Application, name it as per your requirements
Step 2: On AWS Console
Make sure you have configured the Directory services in your AWS account, and you have one EC2 Instance to access it through GUI (Active Directory User and Computer)
On that EC2 download the DUO Security Authentication Proxy from below link. And install the same.
https://dl.duosecurity.com/duoauthproxy-latest.exe
Click on Next
Make sure the Open Authentication Proxy Configuration file is checked.
Once you click on finish it will opens the Configuration file which will looks like the below.
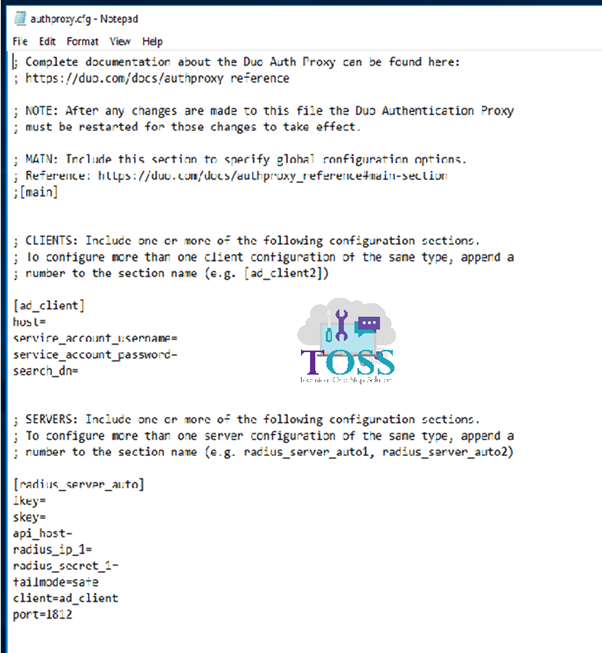
Replace them with the below content.
[duo_only_client]
[radius_server_auto]
ikey=XXX
skey=YYY
api_host=api-ZZZ.duosecurity.com
radius_ip_1=<AD-DNS-address#1>
radius_secret_1=<My-password>
radius_ip_2=<AD-DNS-address#2>
radius_secret_2=<My-password>
failmode=safe
client=duo_only_client
port=1812
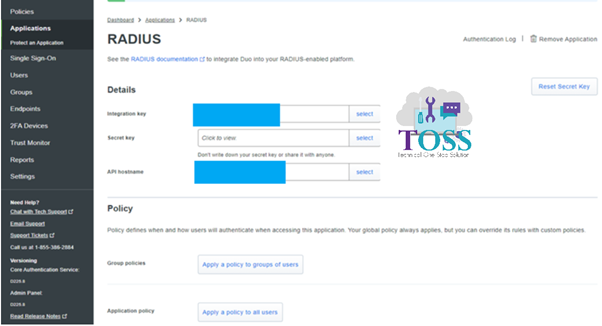
The Below 3 things you will get from the DUO Application, which we have created in the start named as Radius. In Step 1
- Integration key
- Secret key
- API hostname
radius_ip_1 and 2 will get in the Directory Service which is under the DNS address.
radius_secret_1 and 2 will be the admin password of the Directory Service. If you have forgot it you can reset it in the Directory Service screen.

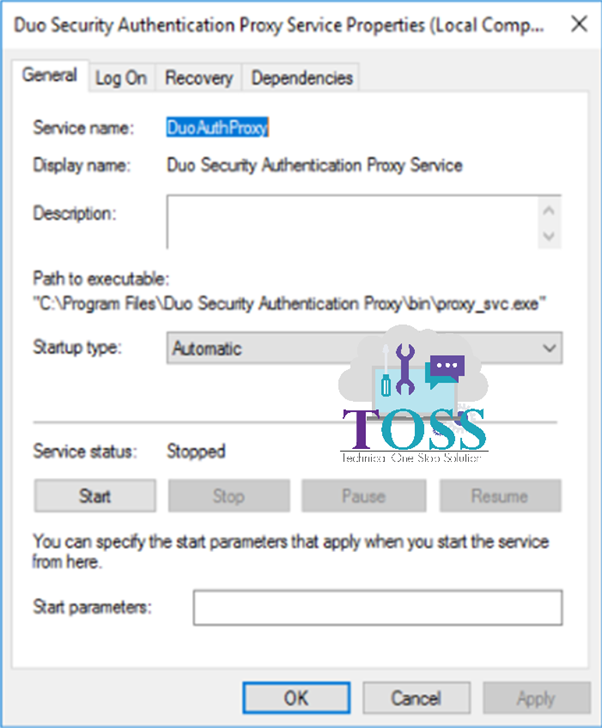
Once all the changes are done, go to the service and make sure DuoAuthProxy(Duo Security Authentication Proxy Service) is running(most of the time it will be in stop state).
Step 3: On AWS Directory Service
Go to Directory Service, in the bottom you will find Multi-Factor Authentication > Click on Actions > Click on Enable
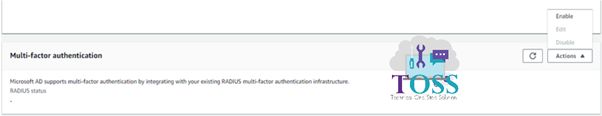
You will get the below screen, fill all the details as mentioned below.
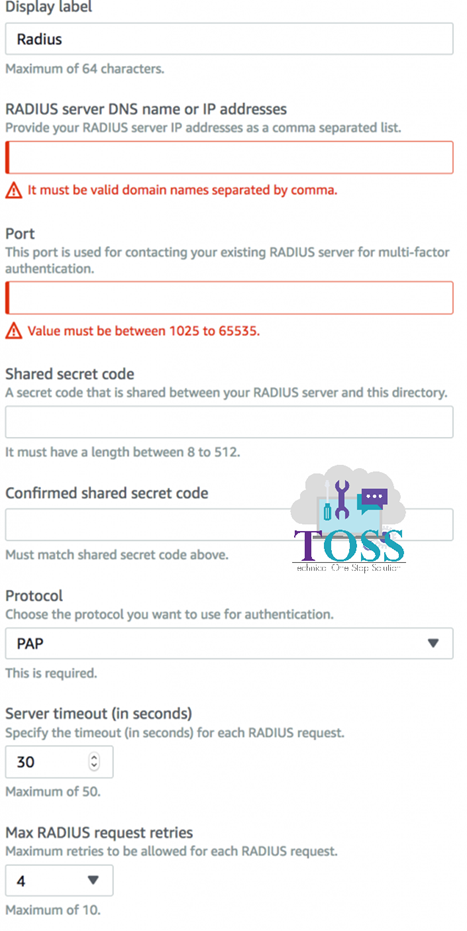
- Display Label: It’s a display name for RADIUS Server Configuration.
- RADIUS server DNS name or one or more IP addresses: Enter the IP addresses of your RADIUS server. If you have more than one RADIUS server, you can enter multiple IP addresses of Radius Server, separated by comma (for example, 192.0.0.0, 192.0.0.12). Alternatively, you can use a DNS name for your RADIUS server. – In our example it will be the tool where we have installed the DUOs Auth Proxy
- Port: Enter the port number of your RADIUS server that you set at the end of Step 2.
- Shared secret code: Enter the same shared secret you created in your RADIUS server. This will be the Directory Service admin password.
- Confirm shared secret code: Re-enter your shared secret code.
- Protocol: Select the authentication protocol between the Microsoft AD and the RADIUS server. Supported protocols are PAP, CHAP MS-CHAPv1, and MS-CHAPv2.
- Server timeout (in seconds): Enter the amount of time to wait for the RADIUS server to respond to authentication requests. If the RADIUS server does not respond in time, authentication is retried (see Max retries). This value must be from 1 to 50. There is no recommended value as it depends on the latency between RADIUS Server and AWS Managed Microsoft AD.
- Max retries: Specify the number of times that communication with the RADIUS server is attempted before failing. This must be a value from 0 to 10.
- Choose Edit to update the RADIUS settings for your directory. The update process takes less than two minutes to complete. When it’s done RADIUS Status changes to Completed.
Make sure the security group is open for 1812 UDP port from the EC2 where you installed the DUO’s Proxy and the directory service.
Once it’s done it will takes approx. 2 minutes to get it up.

Step 4 : On Client VPN Endpoints
Now finally we will be Creating the Client VPN Endpoint Go to VPC > Create Client VPN Endpoint
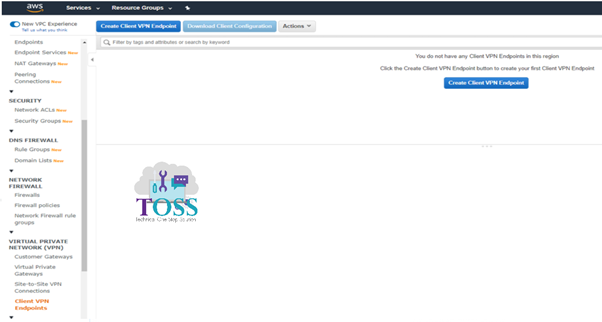
Fill all the details which are required as per your configuration.
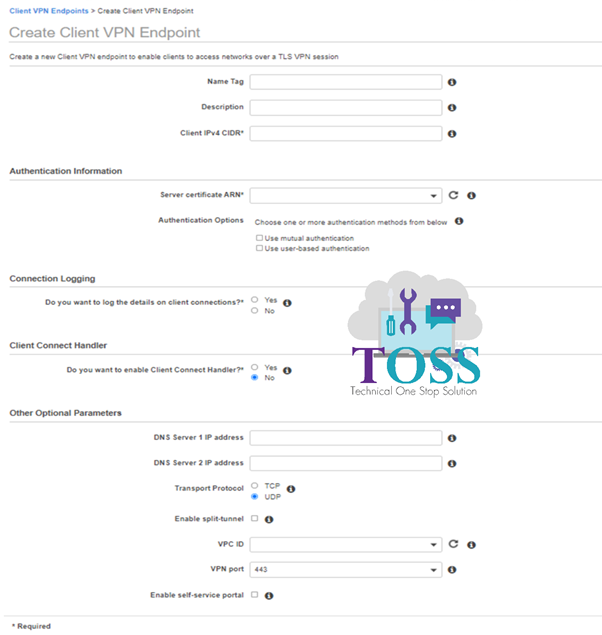
Name Tag: Name of the Client VPN Endpoint
Description: A brief description of the Client VPN endpoint
Client IPV4 CIDR*: The IP address range, in CIDR notation, from which client IP addresses are allocated.
Server Certificate ARN*: The ARN of the server certificate. The server certificate must be provisioned in AWS Certificate Manager (ACM).
Authentication Options: Here select Use user-based authentication > Select Active Directory authentication.
Directory ID*: Select the Directory service where we have configured MFA.
Remain options based on your requirements you can select and deselect them. > Click on Create Client VPN Endpoint
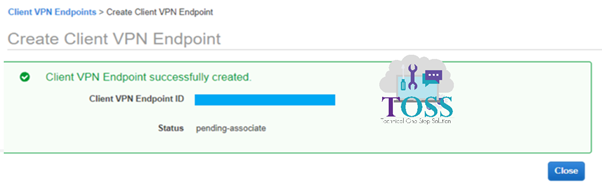
Once Endpoint is created, create the Associate. Add the subnet which is required.

Apply the Security group which will be having an access to RDP or SSH to your EC2 Instances
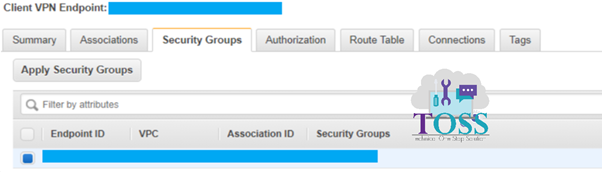
Add the Authorization rule: In this we will be having all the IP address list which we can connect from the VPN.

Make sure all the routing tables are configured as per requirements. Based on the Subnet you have Associated with it will takes the default Route. You can add the manual routing also.

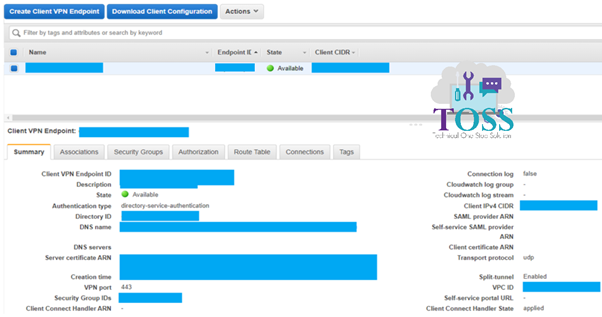
Once all is done Click on Download Client Configuration. Use that configuration in the AWS Client VPN
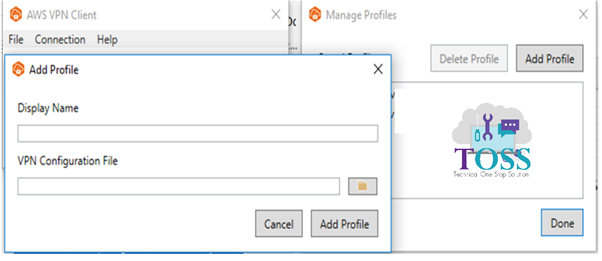
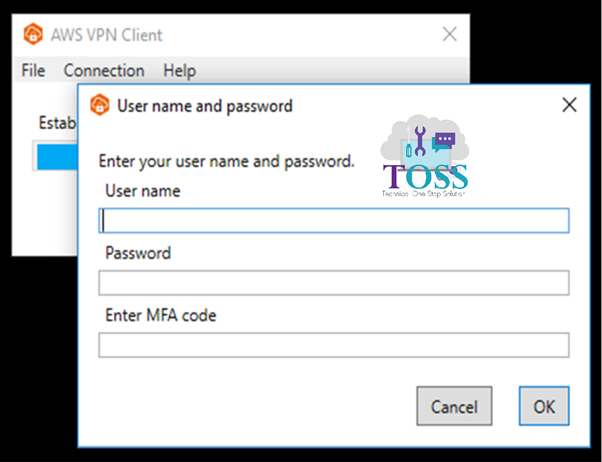
Install AWS VPN Client. Click on File > Manage Profiles > Add Profile > Give the Display name and the VPN Configuration File which is downloaded for the AWS.
Provide your Directory Service Username and password > Make sure it should be added in the DUO’s also
I hope this has helped you in “AWS Client VPN configuring the DUO’s MFA“. Share with your friends and coluges.