Encrypting EBS Volume in AWS
Some times we forgot to encrypt the Volumes while creating an instance. But when Security Team tells we want to encrypt the volume you can follow the below steps which gives you an easy steps to encrypt the Volumes with the less down time. Encrypting EBS Volume in AWS
Click on the Instance which you want to encrypt its drive.
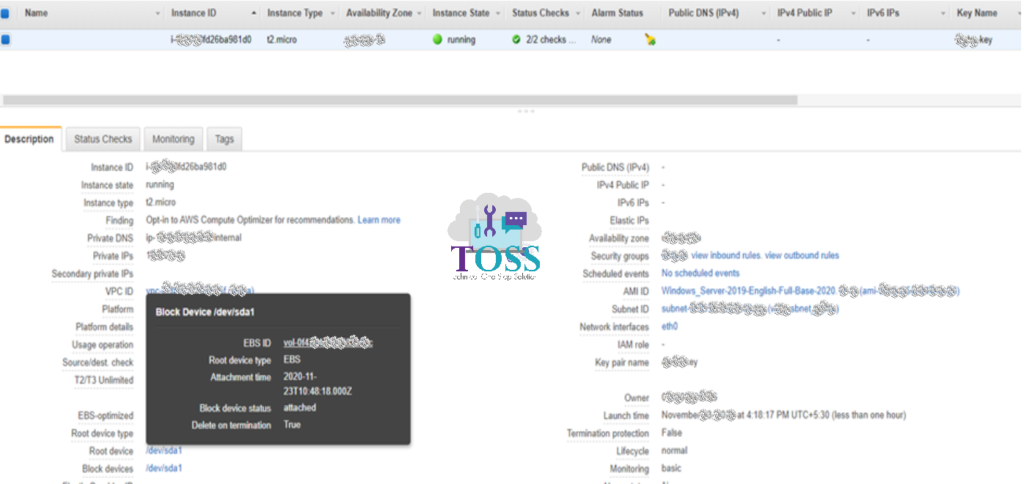
Once you select the instance you will get the Root device and Block devices – Root device is always the C drive in windows and root drive in other OS. the Block devices are additional drives in the system.
When you click on the Root device you will get the EBS ID, which will take you to the volume.
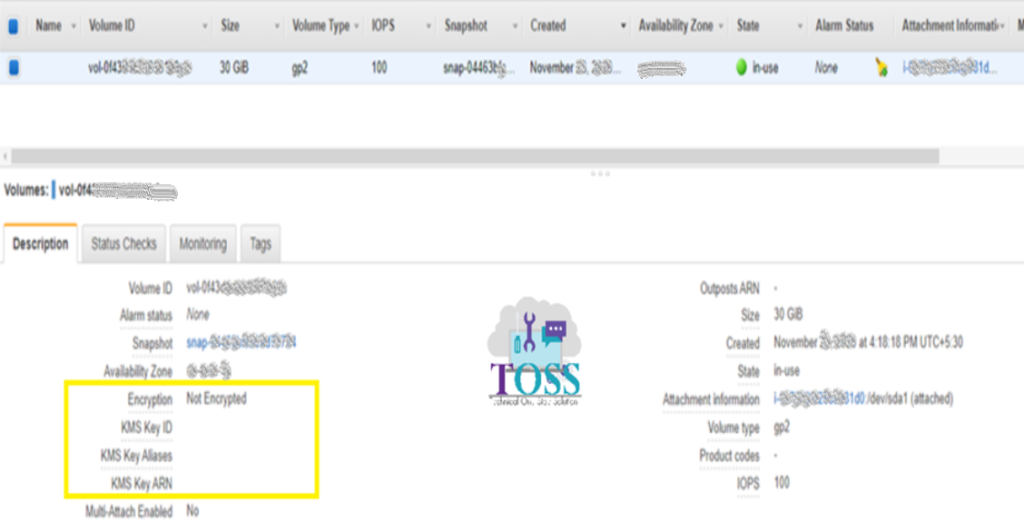
Now this volume is not encrypted. to encrypt this volume > Click on Action and select Create Snapshot

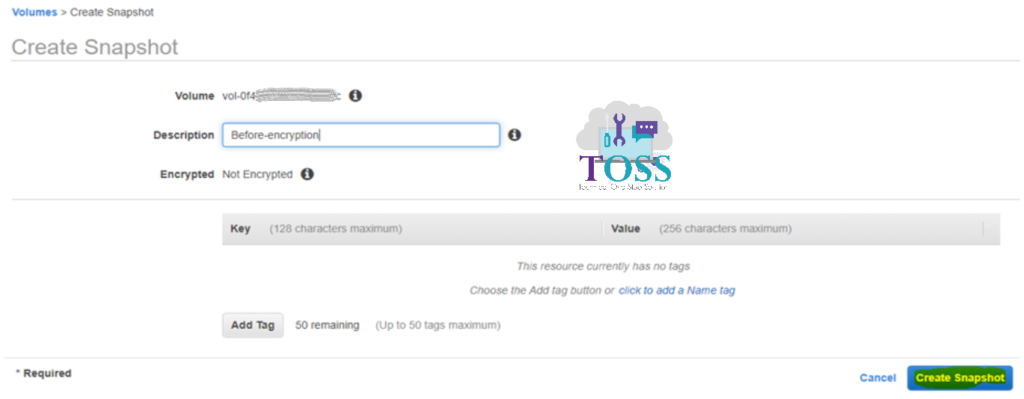
Provide the description of the Snapshot and click on Create Snapshot button.
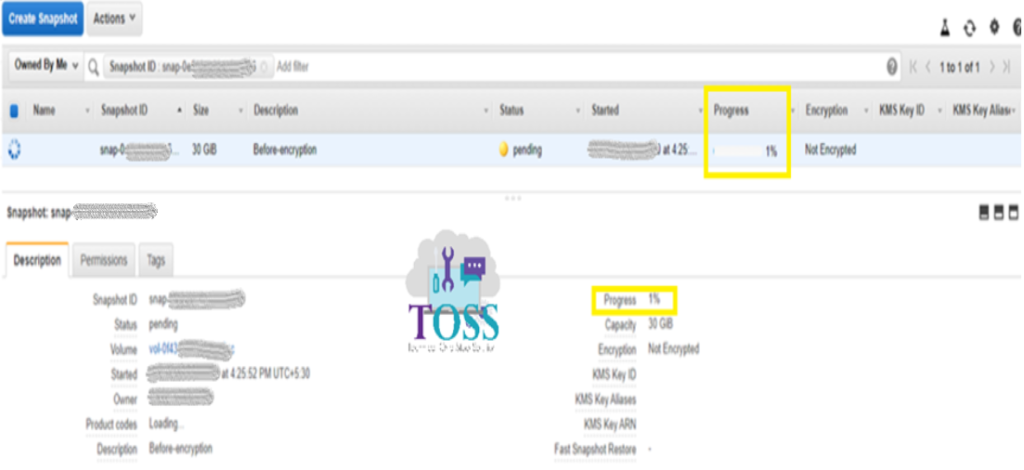
You get the result Create Snapshot Request Succeeded. Click on the Snapshot link so that directly you can go to the Snapshot list.

It will shows the snapshot creation progress in Percentage. And this will be not encrypted.
Once its completed it will shows 100% and available.
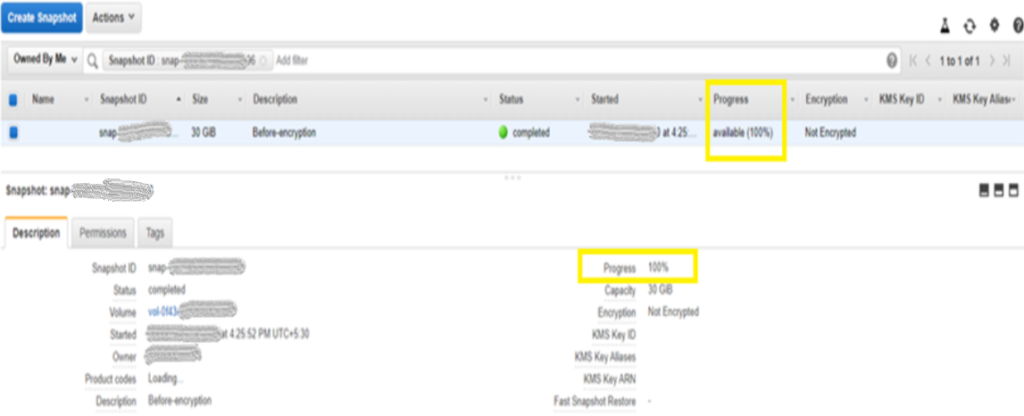
Now this snapshot will be not encrypted. Now Click on Action and Create Volume

Make Sure the Availability zone is as same as the instance. Otherwise while attaching you will face an issue. Enable the check box which is mentioned as “Encrypt the volume“
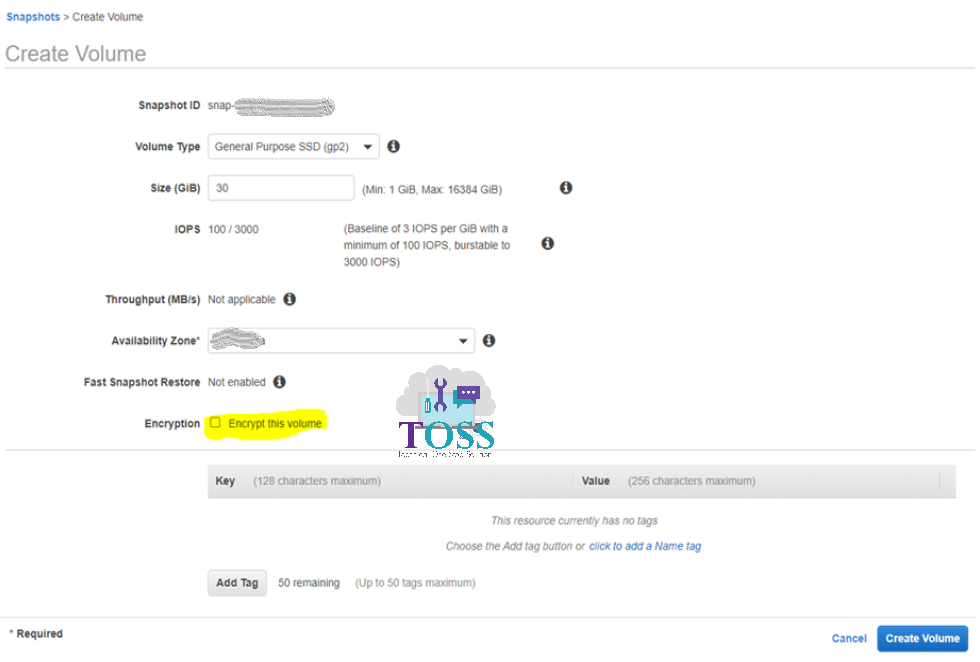
Once the Check box is enabled you will get an additional option for selecting the master key. Provide the KMS key which you can use for encryption. And click on Create volume.
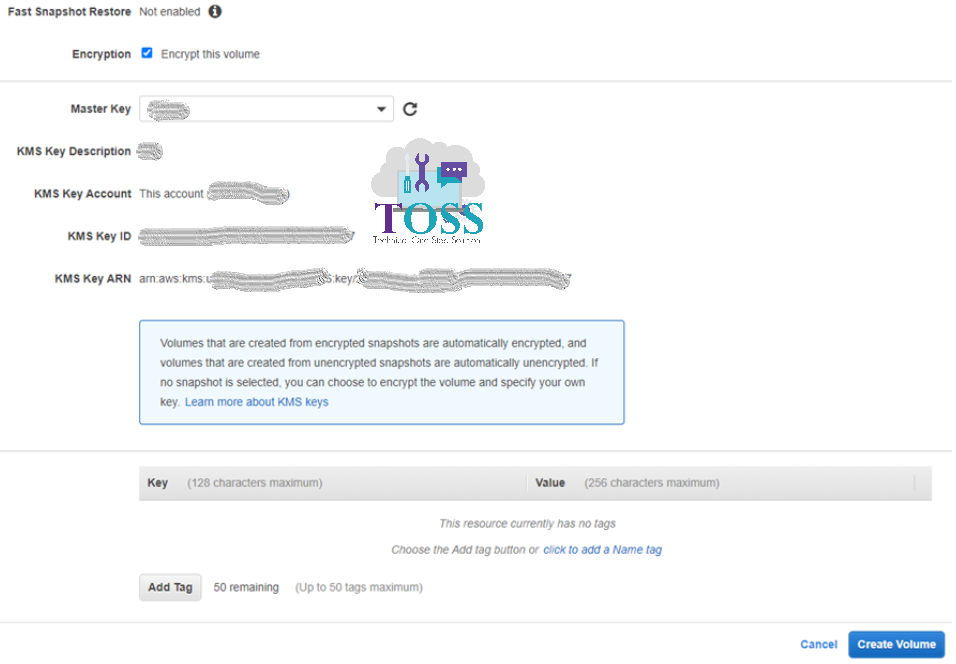
It will redirects to Create Volume Request Succeeded. Click on Volume ID to see the volume.

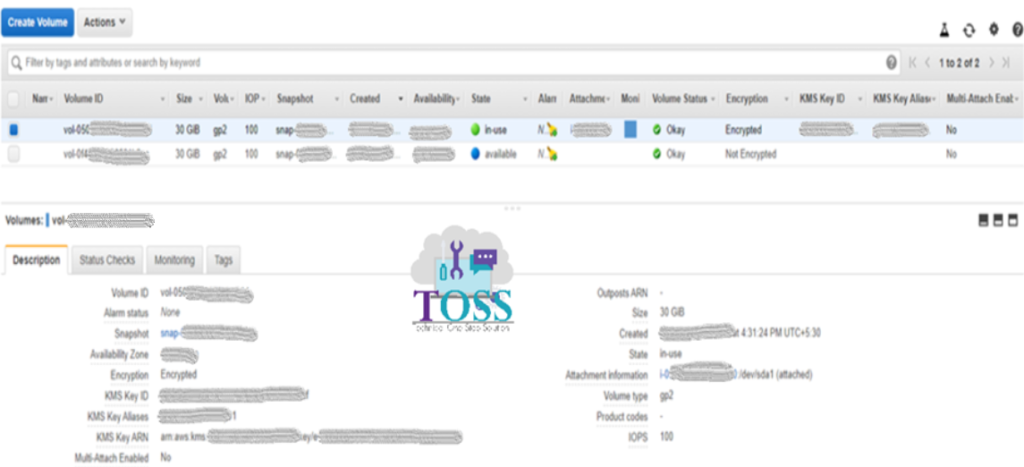
Now you can see both the volume one is encrypted which is created newly using snapshot another one is not encrypted which is still in-use.
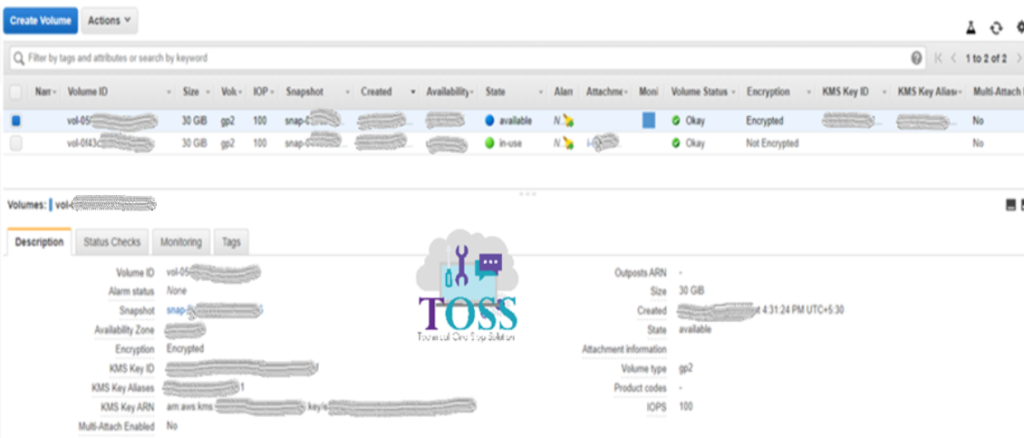
Now we want to detach the old volume(Not-Encrypted) from the instance and attach the new volume(Encrypted)
To detach the Old volume and attach the new volume first you want to stop the instance.
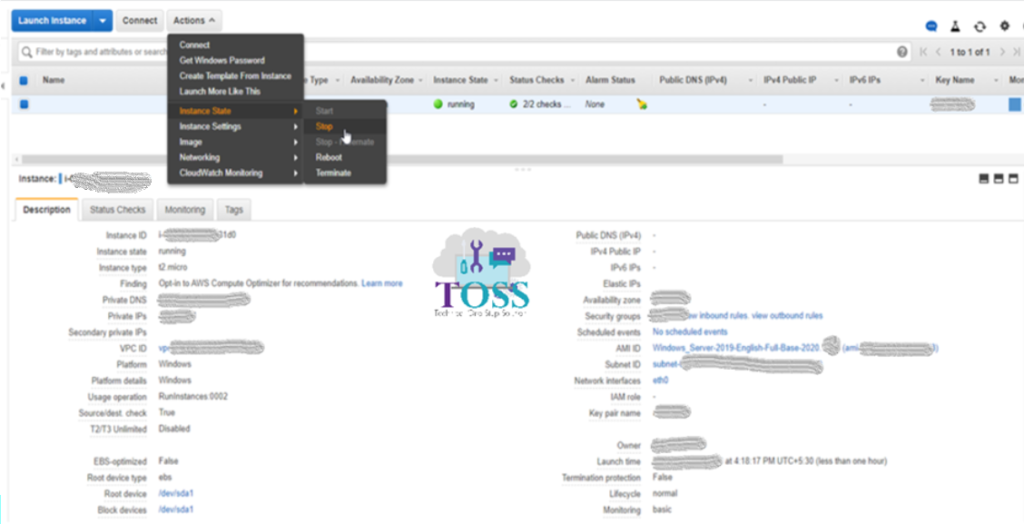
Once the instance has been stopped. Select the volume, click on Actions and click Detach Volume
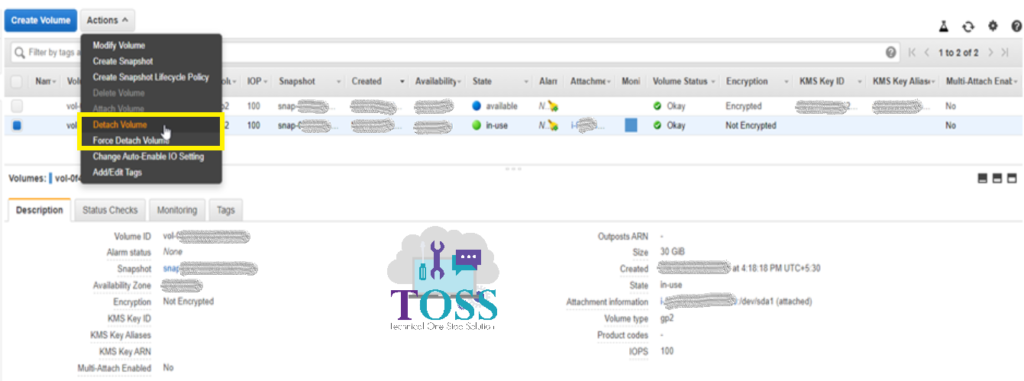
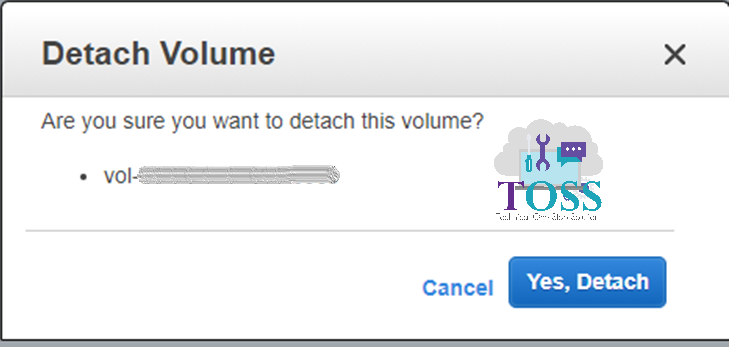
It will ask for the conformation to Detach the volume, press Yes, Detach
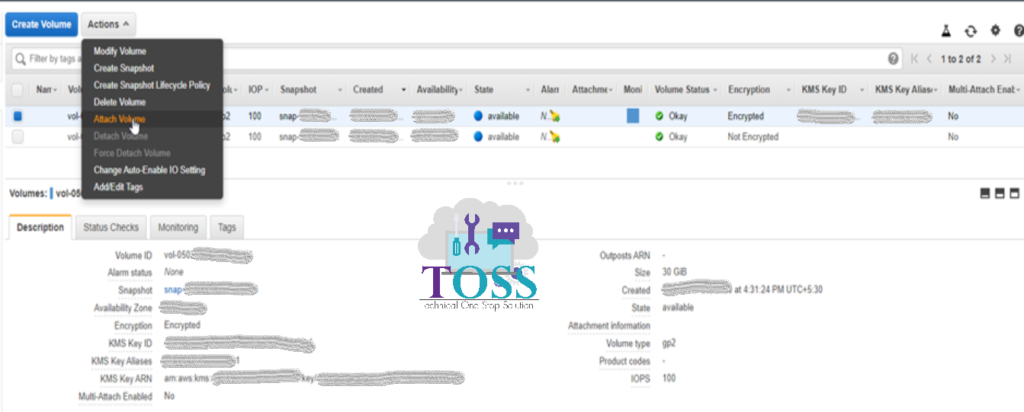
Once you detach the Volume it will be showing the status Available.

Select the encrypted Volume, click on Actions and click Attach Volume
While attaching the Volume it will ask for the Instance ID, Provide the same instance ID(you can use the drop down also to search the instance ID). Give the Device properly, if an small mistake happens in the device means the system will not come up. This you should take from the old volume before detaching from the server.
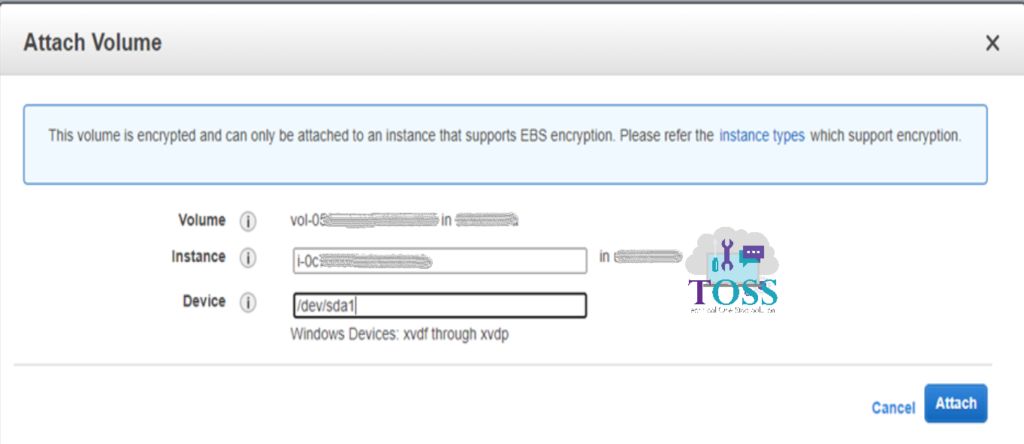
Now you can see the encrypted volume is in-use
Make sure you have attached the Proper IAM role which have an Access to the KMS key which is attached to the EBS volume.
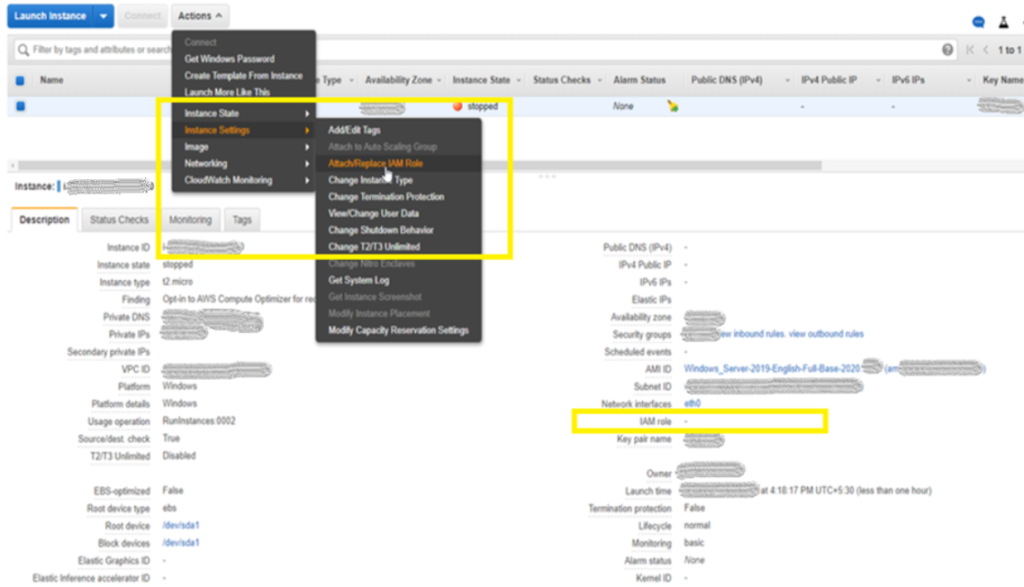
Once the role is attached and the Root Device is attached you can start the instance.
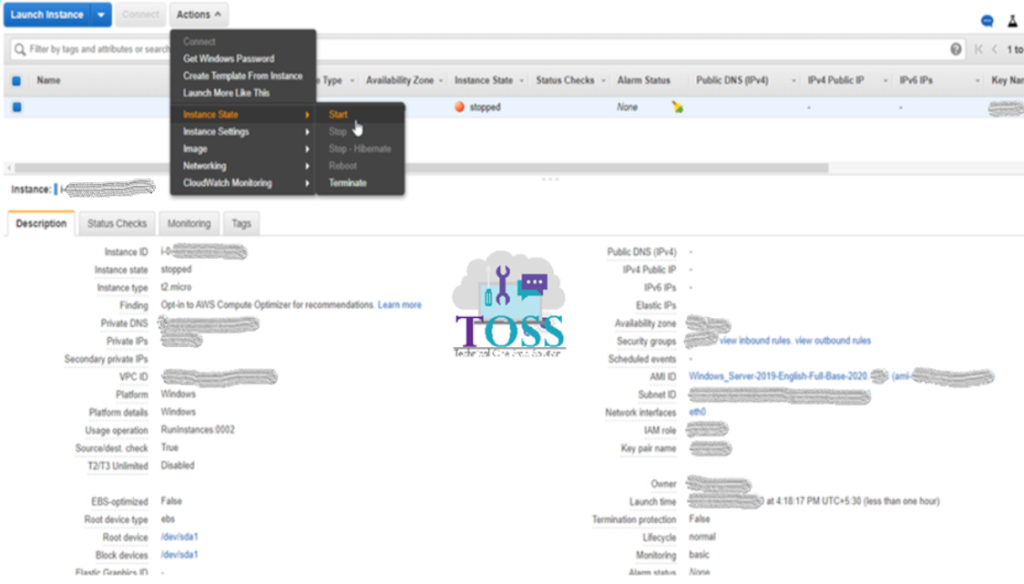
Pop-up will come for starting the instance click on Yes, Start
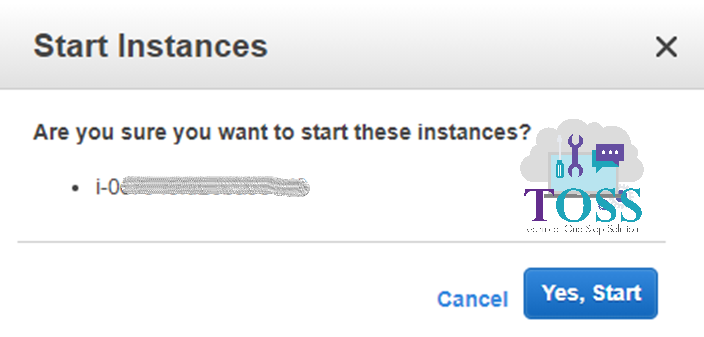
If all the steps followed correctly the instance will come up without any issues.
We hope this blog has helped you in Encrypting Instance EBS Volume in AWS
And also if you required any technology you want to learn, let us know below we will publish them in our site http://tossolution.com/
Like our page in Facebook and follow us for New technical information.