Set-AdfsClaimsProviderTrust
Set-AdfsClaimsProviderTrust is accessible with the help of adfs module. To install adfs on your system please refer to this adfs.
Synopsis
Sets the properties of a claims provider trust.
Description
The Set-AdfsClaimsProviderTrust cmdlet configures the trust relationship with a claims provider.
Parameters
-AcceptanceTransformRules
Specifies the claim acceptance transform rules for accepting claims from this claims provider. These rules determine the information that is accepted from the partner represented by the claims provider trust.
Required? false
Position? named
Default value none
Accept pipeline input? True (ByPropertyName)
Accept wildcard characters? false
-AcceptanceTransformRulesFile <String>
Specifies a file that contains the claim acceptance transform rules for accepting claims from this claims provider.
Required? false
Position? named
Default value none
Accept pipeline input? false
Accept wildcard characters? false
-AllowCreate <Boolean]>
Indicates whether the Security Assertion Markup Language (SAML) parameter AllowCreate is sent in SAML requests to the claims provider. The default value is True.
Required? false
Position? named
Default value none
Accept pipeline input? false
Accept wildcard characters? false
-AlternateLoginID <String>
Specifies the LDAP name of the attribute that you want to use for login.
Required? false
Position? named
Default value none
Accept pipeline input? false
Accept wildcard characters? false
-AnchorClaimType <String>
Required? false
Position? named
Default value none
Accept pipeline input? false
Accept wildcard characters? false
-AutoUpdateEnabled <Boolean]>
Indicates whether changes to the federation metadata by the MetadataURL parameter apply automatically to the configuration of the trust relationship. If this parameter has a value of $True, partner claims, certificates, and endpoints are updated automatically.
Note: When auto-update is enabled, fields that can be overwritten by metadata become read only.
Required? false
Position? named
Default value none
Accept pipeline input? false
Accept wildcard characters? false
-ClaimOffered <ClaimDescription[]>
Specifies an array of claims that are offered by this claims provider.
Required? false
Position? named
Default value none
Accept pipeline input? True (ByValue)
Accept wildcard characters? false
-CustomMFAUri <Uri>
Required? false
Position? named
Default value none
Accept pipeline input? false
Accept wildcard characters? false
-EncryptedNameIdRequired <Boolean]>
Indicates whether the relying party requires that the NameID claim be encrypted. This setting applies to SAML logout requests.
Required? false
Position? named
Default value none
Accept pipeline input? false
Accept wildcard characters? false
-EncryptionCertificate <X509Certificate2>
Specifies the certificate to be used for encrypting a NameID to this claims provider in SAML logout requests. Encrypting the NameID is optional.
Required? false
Position? named
Default value none
Accept pipeline input? false
Accept wildcard characters? false
-EncryptionCertificateRevocationCheck <String>
Specifies the type of validation that occurs for the encryption certificate before it is used for encrypting claims. The acceptable values for this parameter are:
-- None
-- CheckEndCert
-- CheckEndCertCacheOnly
-- CheckChain
-- CheckChainCacheOnly
-- CheckChainExcludeRoot
-- CheckChainExcludeRootCacheOnly
Required? false
Position? named
Default value none
Accept pipeline input? false
Accept wildcard characters? false
-Force <SwitchParameter>
Forces the command to run without asking for user confirmation.
Required? false
Position? named
Default value none
Accept pipeline input? false
Accept wildcard characters? false
-Identifier <String>
Specifies the unique identifier for this claims provider trust. No other trust can use an identifier from this list. Uniform Resource Identifiers (URIs) are often used as unique identifiers for a claims provider trust, but you can use any string of characters.
Required? false
Position? named
Default value none
Accept pipeline input? false
Accept wildcard characters? false
-LookupForests <String[]>
Specifies the forest DNS names that can be used to look up the AlternateLoginID.
Required? false
Position? named
Default value none
Accept pipeline input? false
Accept wildcard characters? false
-MetadataUrl <Uri>
Specifies the URL at which the federation metadata for this claims provider trust is available.
Required? false
Position? named
Default value none
Accept pipeline input? false
Accept wildcard characters? false
-MonitoringEnabled <Boolean]>
Indicates whether periodic monitoring of this claims provider's federation metadata is enabled. The URL of the claims provider's federation metadata is specified by the MetadataUrl parameter.
Required? false
Position? named
Default value none
Accept pipeline input? false
Accept wildcard characters? false
-Name <String>
Specifies the friendly name of this claims provider trust.
Required? false
Position? named
Default value none
Accept pipeline input? false
Accept wildcard characters? false
-Notes <String>
Specifies notes for this claims provider trust.
Required? false
Position? named
Default value none
Accept pipeline input? false
Accept wildcard characters? false
-OrganizationalAccountSuffix <String[]>
Specifies a list of organizational account suffixes that an administrator can configure for the claims provider trust for Home Realm Discovery (HRD) scenarios.
Required? false
Position? named
Default value none
Accept pipeline input? false
Accept wildcard characters? false
-PassThru <SwitchParameter>
Returns an object representing the item with which you are working. By default, this cmdlet does not generate any output.
Required? false
Position? named
Default value none
Accept pipeline input? false
Accept wildcard characters? false
-PromptLoginFallbackAuthenticationType <String>
Required? false
Position? named
Default value none
Accept pipeline input? false
Accept wildcard characters? false
-PromptLoginFederation <Microsoft.IdentityServer.PolicyModel.Configuration.PromptLoginFederation>
The acceptable values for this parameter are:
-- None. Do not federate prompt=login request and error instead.
-- FallbackToProtocolSpecificParameters. Translate prompt=login to wfresh=0 and Wauth=forms during federation. If wauth is present in the original request, it will be preserved.
-- ForwardPromptAndHintsOverWsFederation. Forward prompt, login_hint, and domain_hint parameters during federation.
Required? false
Position? named
Default value none
Accept pipeline input? false
Accept wildcard characters? false
-ProtocolProfile <String>
Specifies which protocol profiles the claims provider supports. The acceptable values for this parameter are:
-- SAML
-- WsFederation
-- WsFed-SAML
Required? false
Position? named
Default value none
Accept pipeline input? false
Accept wildcard characters? false
-RequiredNameIdFormat <Uri>
Specifies the format that is required for NameID claims to be included in SAML requests to the claims provider. By default, no format is required.
Required? false
Position? named
Default value none
Accept pipeline input? false
Accept wildcard characters? false
-SamlAuthenticationRequestIndex <UInt16]>
Specifies the value of AssertionConsumerServiceIndex that is placed in SAML authentication requests that are sent to the claims provider.
Required? false
Position? named
Default value none
Accept pipeline input? false
Accept wildcard characters? false
-SamlAuthenticationRequestParameters <String>
Specifies which of the following parameters to use in SAML authentication requests to the claims provider: AssertionConsumerServiceIndex, AssertitionConsumerServiceUrl, and ProtocolBinding. The acceptable values for this parameter are:
-- None
-- Index
-- Url
-- ProtocolBinding
-- UrlWithProtocolBinding
Required? false
Position? named
Default value none
Accept pipeline input? false
Accept wildcard characters? false
-SamlAuthenticationRequestProtocolBinding <String>
Specifies the value of ProtocolBinding to place in SAML authentication requests to the claims provider. The acceptable values for this parameter are:
-- Artifact
-- POST
-- Redirect
Required? false
Position? named
Default value none
Accept pipeline input? false
Accept wildcard characters? false
-SamlEndpoint <SamlEndpoint[]>
Specifies an array of SAML protocol endpoints for this claims provider.
Required? false
Position? named
Default value none
Accept pipeline input? True (ByValue)
Accept wildcard characters? false
-SignatureAlgorithm <String>
Specifies the signature algorithm that the claims provider uses for signing and verification. The acceptable values for this parameter are:
http://www.w3.org/2000/09/xmldsig#rsa-sha1http://www.w3.org/2001/04/xmldsig-more#rsa-sha256
Required? false
Position? named
Default value none
Accept pipeline input? false
Accept wildcard characters? false
-SignedSamlRequestsRequired <Boolean]>
Indicates whether the Federation Service requires signed SAML protocol requests from the relying party. If you specify a value of $True, the Federation Service rejects unsigned SAML protocol requests.
Required? false
Position? named
Default value none
Accept pipeline input? false
Accept wildcard characters? false
-SigningCertificateRevocationCheck <String>
Specifies the type of certificate validation that occurs when signatures are verified on responses or assertions from the claims provider. The acceptable values for this parameter are:
-- None
-- CheckEndCert
-- CheckEndCertCacheOnly
-- CheckChain
-- CheckChainCacheOnly
-- CheckChainExcludeRoot
-- CheckChainExcludeRootCacheOnly
Required? false
Position? named
Default value none
Accept pipeline input? false
Accept wildcard characters? false
-SupportsMFA <SwitchParameter>
Required? false
Position? named
Default value none
Accept pipeline input? false
Accept wildcard characters? false
-TargetCertificate <X509Certificate2>
Specifies the certificate of the claims provider trust that is modified by the cmdlet.
Required? true
Position? named
Default value none
Accept pipeline input? True (ByValue)
Accept wildcard characters? false
-TargetClaimsProviderTrust <ClaimsProviderTrust>
Specifies a ClaimsProviderTrust object. The cmdlet modifies the claims provider trust that you specify. To obtain a ClaimsProviderTrust object, use the Get-AdfsClaimsProviderTrust cmdlet.
Required? true
Position? named
Default value none
Accept pipeline input? True (ByValue)
Accept wildcard characters? false
-TargetIdentifier <String>
Specifies the identifier of the claims provider trust that is modified by the cmdlet.
Required? true
Position? named
Default value none
Accept pipeline input? True (ByValue)
Accept wildcard characters? false
-TargetName <String>
Specifies the friendly name of the claims provider trust that is modified by the cmdlet.
Required? true
Position? named
Default value none
Accept pipeline input? True (ByValue)
Accept wildcard characters? false
-TokenSigningCertificate <X509Certificate2[]>
Specifies an array of token-signing certificates that the claims provider use.
Required? false
Position? named
Default value none
Accept pipeline input? false
Accept wildcard characters? false
-WSFedEndpoint <Uri>
Specifies the WS-Federation Passive URL for this claims provider.
Required? false
Position? named
Default value none
Accept pipeline input? false
Accept wildcard characters? false
-Confirm <SwitchParameter>
Prompts you for confirmation before running the cmdlet.Prompts you for confirmation before running the cmdlet.
Required? false
Position? named
Default value false
Accept pipeline input? false
Accept wildcard characters? false
-WhatIf <SwitchParameter>
Shows what would happen if the cmdlet runs. The cmdlet is not run.Shows what would happen if the cmdlet runs. The cmdlet is not run.
Required? false
Position? named
Default value false
Accept pipeline input? false
Accept wildcard characters? falseSyntax
Set-AdfsClaimsProviderTrust [-Name <String>] [-Identifier <String>] [-SignatureAlgorithm <String>] [-TokenSigningCertificate <X509Certificate2[]>] [-MetadataUrl <Uri>] [-AcceptanceTransformRules <String>] [-AcceptanceTransformRulesFile <String>] [-AllowCreate <Boolean>] [-AutoUpdateEnabled <Boolean>] [-WSFedEndpoint <Uri>] [-EncryptionCertificate <X509Certificate2>] [-EncryptionCertificateRevocationCheck <String>] [-MonitoringEnabled <Boolean>] [-Notes <String>] [-OrganizationalAccountSuffix <String[]>] [-ClaimOffered <ClaimDescription[]>] [-SamlEndpoint <SamlEndpoint[]>] [-ProtocolProfile <String>] [-RequiredNameIdFormat <Uri>] [-EncryptedNameIdRequired <Boolean>] [-SignedSamlRequestsRequired <Boolean>] [-SamlAuthenticationRequestIndex <UInt16>] [-SamlAuthenticationRequestParameters <String>] [-SamlAuthenticationRequestProtocolBinding <String>] [-SigningCertificateRevocationCheck <String>] -TargetClaimsProviderTrust <ClaimsProviderTrust> [-PassThru] [-WhatIf] [-Confirm] [<CommonParameters>]
Set-AdfsClaimsProviderTrust [-Name <String>] [-Identifier <String>] [-SignatureAlgorithm <String>] [-TokenSigningCertificate <X509Certificate2[]>] [-MetadataUrl <Uri>] [-AcceptanceTransformRules <String>] [-AcceptanceTransformRulesFile <String>] [-AllowCreate <Boolean>] [-AutoUpdateEnabled <Boolean>] [-WSFedEndpoint <Uri>] [-EncryptionCertificate <X509Certificate2>] [-EncryptionCertificateRevocationCheck <String>] [-MonitoringEnabled <Boolean>] [-Notes <String>] [-OrganizationalAccountSuffix <String[]>] [-ClaimOffered <ClaimDescription[]>] [-SamlEndpoint <SamlEndpoint[]>] [-ProtocolProfile <String>] [-RequiredNameIdFormat <Uri>] [-EncryptedNameIdRequired <Boolean>] [-SignedSamlRequestsRequired <Boolean>] [-SamlAuthenticationRequestIndex <UInt16>] [-SamlAuthenticationRequestParameters <String>] [-SamlAuthenticationRequestProtocolBinding <String>] [-SigningCertificateRevocationCheck <String>] -TargetCertificate <X509Certificate2> [-PassThru] [-WhatIf] [-Confirm] [<CommonParameters>]
Set-AdfsClaimsProviderTrust [-Name <String>] [-Identifier <String>] [-SignatureAlgorithm <String>] [-TokenSigningCertificate <X509Certificate2[]>] [-MetadataUrl <Uri>] [-AcceptanceTransformRules <String>] [-AcceptanceTransformRulesFile <String>] [-AllowCreate <Boolean>] [-AutoUpdateEnabled <Boolean>] [-WSFedEndpoint <Uri>] [-EncryptionCertificate <X509Certificate2>] [-EncryptionCertificateRevocationCheck <String>] [-MonitoringEnabled <Boolean>] [-Notes <String>] [-OrganizationalAccountSuffix <String[]>] [-ClaimOffered <ClaimDescription[]>] [-SamlEndpoint <SamlEndpoint[]>] [-ProtocolProfile <String>] [-RequiredNameIdFormat <Uri>] [-EncryptedNameIdRequired <Boolean>] [-SignedSamlRequestsRequired <Boolean>] [-SamlAuthenticationRequestIndex <UInt16>] [-SamlAuthenticationRequestParameters <String>] [-SamlAuthenticationRequestProtocolBinding <String>] [-SigningCertificateRevocationCheck <String>] -TargetIdentifier <String> [-PassThru] [-WhatIf] [-Confirm] [<CommonParameters>]
Set-AdfsClaimsProviderTrust [-Name <String>] [-Identifier <String>] [-SignatureAlgorithm <String>] [-TokenSigningCertificate <X509Certificate2[]>] [-MetadataUrl <Uri>] [-AcceptanceTransformRules <String>] [-AcceptanceTransformRulesFile <String>] [-AllowCreate <Boolean>] [-AutoUpdateEnabled <Boolean>] [-WSFedEndpoint <Uri>] [-EncryptionCertificate <X509Certificate2>] [-EncryptionCertificateRevocationCheck <String>] [-MonitoringEnabled <Boolean>] [-Notes <String>] [-OrganizationalAccountSuffix <String[]>] [-ClaimOffered <ClaimDescription[]>] [-SamlEndpoint <SamlEndpoint[]>] [-ProtocolProfile <String>] [-RequiredNameIdFormat <Uri>] [-EncryptedNameIdRequired <Boolean>] [-SignedSamlRequestsRequired <Boolean>] [-SamlAuthenticationRequestIndex <UInt16>] [-SamlAuthenticationRequestParameters <String>] [-SamlAuthenticationRequestProtocolBinding <String>] [-SigningCertificateRevocationCheck <String>] -TargetName <String> [-PassThru] [-WhatIf] [-Confirm] [<CommonParameters>]
Notes
The claims provider collects and authenticates a user’s credentials, builds up claims for that user, and packages the claims into security tokens or Information Cards. In other words, a claims provider represents the organization for whose users the claims provider issues security tokens or Information Cards on their behalf. When you configure Active Directory Federation Services (AD FS) 2.0, the role of the claims provider is to enable its users to access resources that are hosted in a relying party organization by establishing one side of a federation trust relationship. After the trust is established, tokens and Information Cards can be presented to a relying party across the federation trust.
—————————Example 1—————————
Enable auto-update for a claims provider trust
PS C:> Set-ADFSClaimsProviderTrust -TargetName “TOSSolution claims provider” -AutoUpdateEnabled $False
This command enables auto-update for the claims provider trust named TOSSolution claims provider.
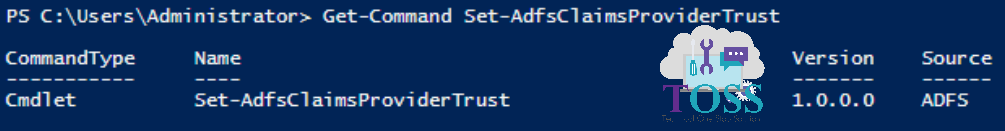
You can check the Version, CommandType and Source of this cmdlet by giving below command.
Get-Command Set-AdfsClaimsProviderTrust
You can also read about
- Disable-AdfsClaimsProviderTrust
- Enable-AdfsClaimsProviderTrust
- Get-AdfsClaimsProviderTrust
- Remove-AdfsClaimsProviderTrust
- Update-AdfsClaimsProviderTrust